

Logical Controls In Information Security
Exploring ways to align with security teams, meet compliance regulations, and free up time in your day?
If you have a hybrid workforce or remote workers accessing proprietary data, you already know that passwords aren’t sufficient for protecting users from various security threats. Plus, aren’t you tired of all the cumbersome password resets, when you have plenty of high value work on your plate?
Multi Factor Authentication
Ensure You Know Who is Accessing Your Company’s Data and IP
- Prevent security breaches
- Reduce support time for password resets and low level IT tasks
- Control access to computers, websites and apps via a single credential
- Enroll employees in seconds onsite or remote for secure access control
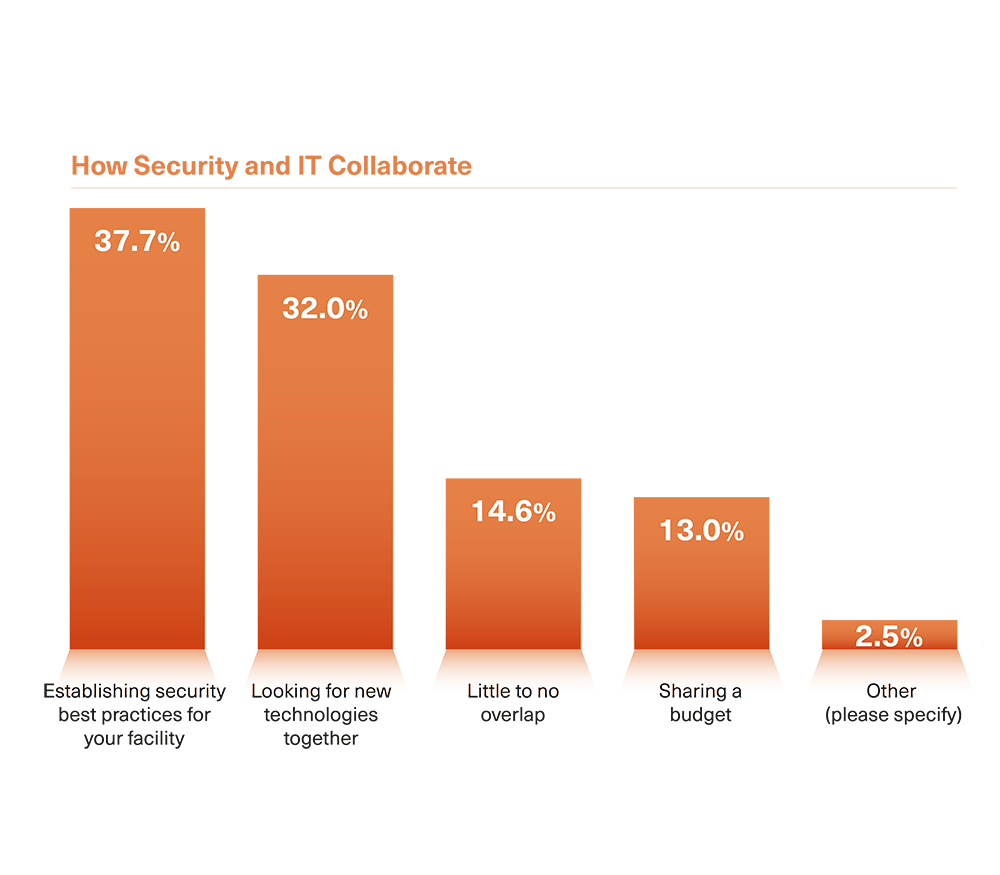
Just 38% of organizations list “Establishing Best Security Practices” as the main way IT & Security Departments collaborate.
With the growing convergence of IT and Security, we work as a bridge between teams. We ensure common goals are met to keep organizations secure, while meeting industry compliance standards.
Key features of a robust MFA solution include:
- Deployable on Windows Active Directory or LDS server
- User-friendly interface for easy self-enrollment of credentials and authentication policy enforcement
- Provides a browser-based SSO Portal for accessing SAML-enabled apps
- Offers an optional Password Manager feature to securely store, update and auto-fill passwords
- Available in a variety of Configurations: SSO and Windows Logon
- Support services to assist IT teams with implementation and ongoing maintenance to ensure compliance for their workforce.
Logical Access Control
Digital Controls for Electronic Access to Devices, Websites & Apps
As physical and logical access technologies become more integrated, ADVANTIDGE helps bridge your IT & security needs to meet compliance regulations and keep your company’s data and people protected.
With Multi-Factor Authentication, we help corporations balance security and usability, with a wide array of authentication factors. This includes one-time passwords, mobile-based push, smartcards, USB keys, risk- and context-based methods, and biometrics, such as fingerprint, face, and behavioral keystroke.
Our consultative approach starts with a technical assessment to understand your requirements for industry compliance. This leads to smart questions that uncover what technology platforms need to be secured for users at all levels including computer logon, website access and app login.

Company Work Environment
Is your IT department managing a combination of in-person, remote and hybrid workforce? You need an easily deployable solution with a single credential for everyone who access proprietary and sensitive company resources. By working alongside security teams, the same unique identifier for physical access can be merged with logical access and enable IT with the tools to meet expectations for security and efficiency regardless of where your workforce resides.
Industry Specific Compliance Regulations
HIPAA for Healthcare, CMMC or NIST SP800-171 for Government Contractors, SOC 2 for technology companies. The list of industry specific regulations for compliance have become more common and complex. You need a partner that understands the needs for your organization based on the unique technical environment for your operations. Identifying your workforce and having confidence in your authentication process for users is critical for meeting compliance while maintaining security and productivity for your teams.

Company platforms used to access proprietary data
Regardless of whether you are focused on SSO or Windows Logon, multiple solutions exist that can be quickly deployed without disrupting productivity for your workforce while relying on a variety of authentication methods. Additionally as more companies shift to the cloud, control of website logins and access to SaaS platforms or apps can be managed from a single dashboard by IT teams tasked with ensuring security for important company functions.
Request a consultation to learn how we can help you meet security & compliance requirements, today and in the future.
WHAT CLIENTS SAY ABOUT US
Customer Feedback



