Cybersecurity breaches are not a matter of if, they’re a matter of when.
In Verizon’s 2021 Data Breach Investigation Report, phishing remains one of the top security threats and has increased to 36% of breaches, up from 25% last year. The increase correlates with the massive shift to work-from-home employees following the pandemic.
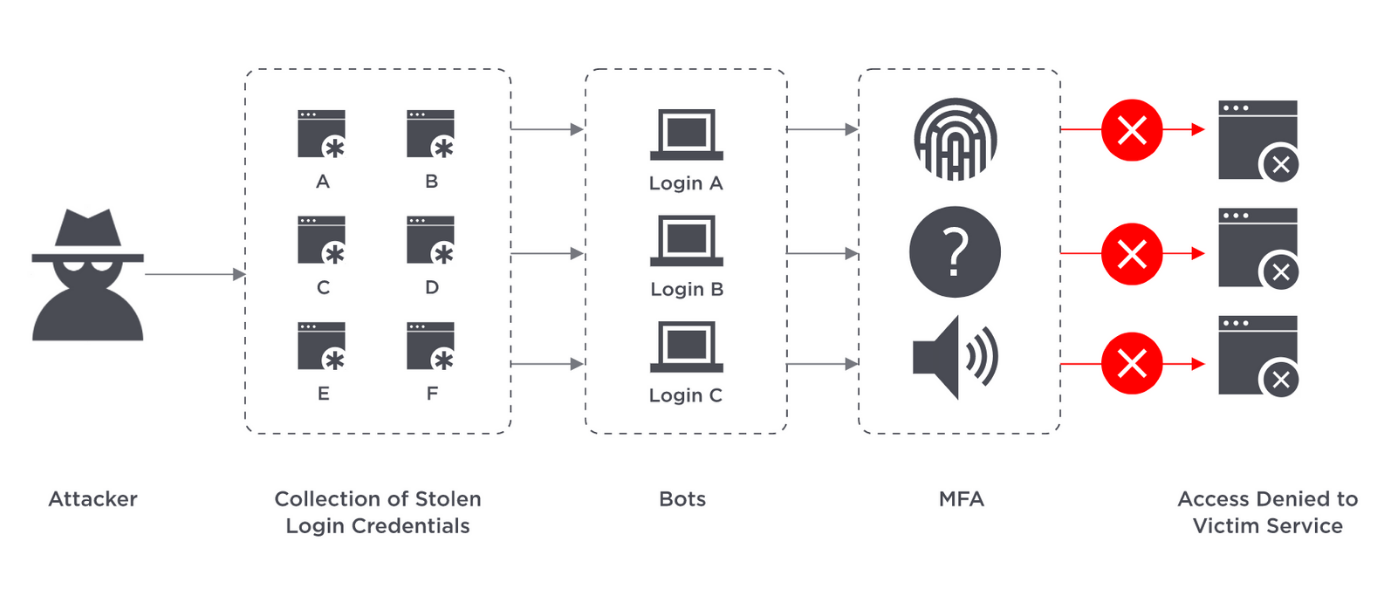
Criminals target employees with emails, texts, or ads, impersonating legitimate organizations to steal their credentials — and use them to penetrate your network.
In the table below 61% of breaches involved credentials, which phishing continues to go hand-in-hand with stolen credentials.

This data is sadly projected to increase as the adaptation to remote workforces has taken precedence. The need for better logical access control parallels this projection.
Not only are targeted phishing attacks among the most common logical access breaches but they are cited by 77% of respondents as their top-level concern:

As cyber-attacks are inevitable and on the rise, IT and security departments are under immense pressure to adopt better technologies to combat these threats. One of the best and most secure ways IT defends against phishing and resource hacking is through multi-factor authentication.
Two Ways Multi-Factor Authentication Combats Cyber Threats:
-
Phishing
If a hacker launches a phishing attempt to steal one of your employee’s credentials, and you’ve implemented MFA, the hacker won’t be able to gain access. ADVANTIDGE multi-factor authentication leverages credentials such as one-time passwords (OTPs) sent to another device (e.g. a mobile phone), fingerprints, or other biometric factors that are required to gain access, and attackers won’t have all that.
Aspects of our MFA solutions, such as DigitalPersona, require the user to enter something they have, something they are, and something they know; attackers won’t have all of those details thus protecting your system and users.
-
Ransomware
Ransomware attacks are initiated once a hacker can gain access to account credentials. When ADVANTIDGE ActivID multi-factor authentication is deployed, IT admins will get notified if there are any unauthorized login attempts. IT can take immediate action to keep attackers out when unexpected authorizations are requested.
Organizations can prevent ransomware attacks and protect themselves from expensive extortion demands when many methods of authentication are in place for every team member.
Why is Cloud MFA Important to Add with On-Prem MFA?
With the increase in hybridized workforces, IT has to ensure their in-house and WFH employees stay current on risks, by investing in appropriate software and equipment for access control. However, when transferring to cloud-delivered MFA, IT can outsource these solutions to trusted experts, like ADVANTIDGE. We can integrate multi-factor authentication for both cloud-based applications as well as on-prem access control, with customized credentials for your employees. This way, you can have peace of mind that your team at home, or in the office, are gaining access to company resources via the same secured pathway.
Additionally, if your enterprise works with third parties, partners, or vendors onsite or online, enabling MFA will allow your organization control over who has access to your systems and in what capacity. Given that many documents or proprietary data need to be accessed by multiple roles, securing each window of access by using MFA can immensely limit the risk of data breaches.
Talk to ADVANTIDGE today to see how we can empower your IT team, and stop threats in their tracks, with our Multi-Factor Authentication solutions.


