
Responsibilities for implementing enterprise security systems have largely shifted to the duties of IT departments. While technological advances in security have helped keep organizations secure, criminals and bad actors are still getting smarter and savvier. And unfortunately, in this day and age with an ongoing pandemic, the regularity of security breaches and malpractice, organizations are looking to security partners to mitigate as much risk as possible with visitor management systems.
Your top priority is protecting your people first, property, and data, from harm. To take a step in that direction requires identifying how to manage the most common on-prem security threats.
Workplace Threats & How to Mitigate Them With Visitor Management Systems:
Does your office building still use paper clipboards or spreadsheets to manage visitor sign-in processes? Issuing easily cloneable badges for restricted areas of the building are also far too common. Unfortunately, these outdated security measures are easy to breach, and no one likes to admit that. Taking into account human error, glitchy legacy systems, non-automated processes, and disconnected communication; there are tons of ways your organization can be vulnerable to threats. Such as:
Unauthorized Access to Sensitive Areas & Data
How does your organization authorize physical access to certain parts of your facility? How do you verify only your IT team has access to the server room? When the wrong person gains access to your assets, not only is your ability to conduct your business in jeopardy, but your reputation and livelihood is also on the line.
In hospitals, government buildings, schools, and corporations; you not only have important data stored on prem but you also have important people that need to do their jobs unencumbered.
ADVANTIDGE Visitor Management Systems; can automate & verify people’s identity by scanning their driver’s license or government ID to ensure proper authorization is set up for sensitive areas. Customize your VMS database so whether it’s a visitor, patient’s guest, contractor or third party, you can track who they are, why they are there, and where they are allowed to go.
Workplace Violence
Do your team members work in the frontlines of the healthcare or social service industry where the threat of workplace violence is high? With certain work environments prone to stressful circumstances, employee safety & their ability to do their jobs can be at risk. Even more disheartening, is the rise of active shootings in businesses, campuses, and schools in our country.
People are just trying to do their jobs, and part of your job is finding and applying the best security solutions to mitigate the risk of threats. By implementing a visitor management system to track who is at your facility and for what reason, you can help protect your employees and customers from ill intentioned intruders & violent actors. Be the reason your team is properly protected so everyone can have peace of mind at work.
Theft
Despite thinking otherwise, office theft is incredibly common, on the rise, and costs businesses up to $50 billion dollars annually. (Statistic Brain 21). If items are left unattended within the facility or on campus, or important documents are improperly disposed of, and there’s opportunities for swiping… unfortunately some will take advantage.
As an IT professional, you might be less concerned with smaller office supplies like pencils or staplers being nabbed, but when company laptops and hard drives go missing, that presents a much bigger problem. A problem that falls in your lap. Who got access to the server room, how and when? Was there an unauthorized visitor in your boss’s office and now she’s asking you how that could have happened?
With a Visitor Management Solution; not only can you log who’s coming in and out of your building, where they are, and when they leave, in case you need to track down missing items, but you can also check if one of your employees proves not to be trusted after all.
Workplace Emergencies
Every business deals with the threat of an emergency. How well they can deal with emergencies is another matter. Additionally, there are several types of emergencies. While the chance of fires, flooding, acts of terrorism, chemical spills, dangerous equipment malfunctions, or weather-related emergencies are far less common to occur, they present the greatest risk of all.
How confident are you with your organization’s ability to prevent, detect, or respond to an emergency?
In the event of an evacuation how do you know if everyone made it out safely? Do you know what type of visitors are at your facility and where they are at any given time?
With a Visitor Management System in place, you can track where your people are while they are inside, whether its guests or co-workers, so emergency responders know exactly where to find someone if they need rescuing.
________
You may be well equipped to handle emergencies and have your workforce informed on the process. You may have proper controls at entry points and can manage authorizations seamlessly.
However, if you’re still using old school clip board check-ins for visitors or paper processes that don’t supply actionable data in case of an emergency, it’s time to talk to ADVANTIDGE.
We offer industry specific systems: visitor management for corporate, visitor management for healthcare, visitor management for government, & visitor management for municipality.
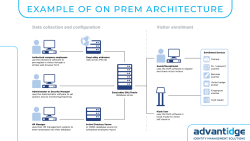
Take a look below at an example of on-prem VMS architecture to get a sense of the tools available to you, how the system communicates, and how easy it is for you and your team to operate:
Empower your workforce to safely & confidently do their jobs without the threat of system breaches, disruption, or violence.
Click Here to Customize your Visitor Management System to fit your facility’s unique needs and customer interfacing processes.


