Read the most recent articles
The world is changing more rapidly than ever.

WFH Is Not For Every Business | How To Prepare Your Organization For Reopening
For many organizations such as manufacturing, healthcare, or utility & energy workers, working from home amidst a pandemic was never an option for these essential in-person industries. While we continue to see supply chain delays, overwhelmed hospitals, and energy crises, we have to do our best to support businesses on the frontlines, as well as… View Article

Religious Temple Upgrades Physical Access Control For Improved Security
Overview: A Jewish Temple first came to ADVANTIDGE back in 2015 to assist with improving security as part of a major construction upgrade to their Culver City campus. The existing security system included outdated, low-resolution, CCTV cameras that didn’t provide sufficient visibility to the staff or security team. The door entry system was only supported… View Article

Financial Institution Incorporates Enterprise Level Visitor Management at Corporate Headquarters and Regional Offices
Overview: Prior to the pandemic, ADVANTIDGE worked with a regional security integrator to implement a new visitor management solution for a financial institution. With over a decade spent building this relationship, ADVANTIDGE provided expertise on complex identification solutions, enabling the integrator to bring increased value to their customers. Consequently, they’ve implemented everything from secure badge… View Article

How to Build a High Volume Enterprise ID Badge System
Enterprise Level ID Systems Does your organization have multiple sites, departments, role functions, and thousands of employees to identify? Are you growing, acquiring or merging other companies and need to integrate multiple systems for secure identification? Or are you challenged with managing industry compliance across multiple business units that are now under one corporate entity? … View Article

Managing Security and Identification for Hybrid Workforces
The Hybrid Preference With the influx of organizations re-opening their offices across industries, leadership teams have to balance the desires of their employees with the best path to productivity and growth for their business. Pew Research surveys show that 64% of employees that started working from home due to the pandemic, claim it improves… View Article

Is Your Legacy Technology Preventing You From Achieving FINRA Compliance?
As cyber-attacks and security breaches continue to evolve and escalate, businesses across industries are required to update their security measures to parallel the growing risk to their operations. Like many industries that have dedicated security compliance requirements, financial organizations need to meet FINRA compliance. Within finance, manufacturing, healthcare, and large enterprises, there are similarities in… View Article
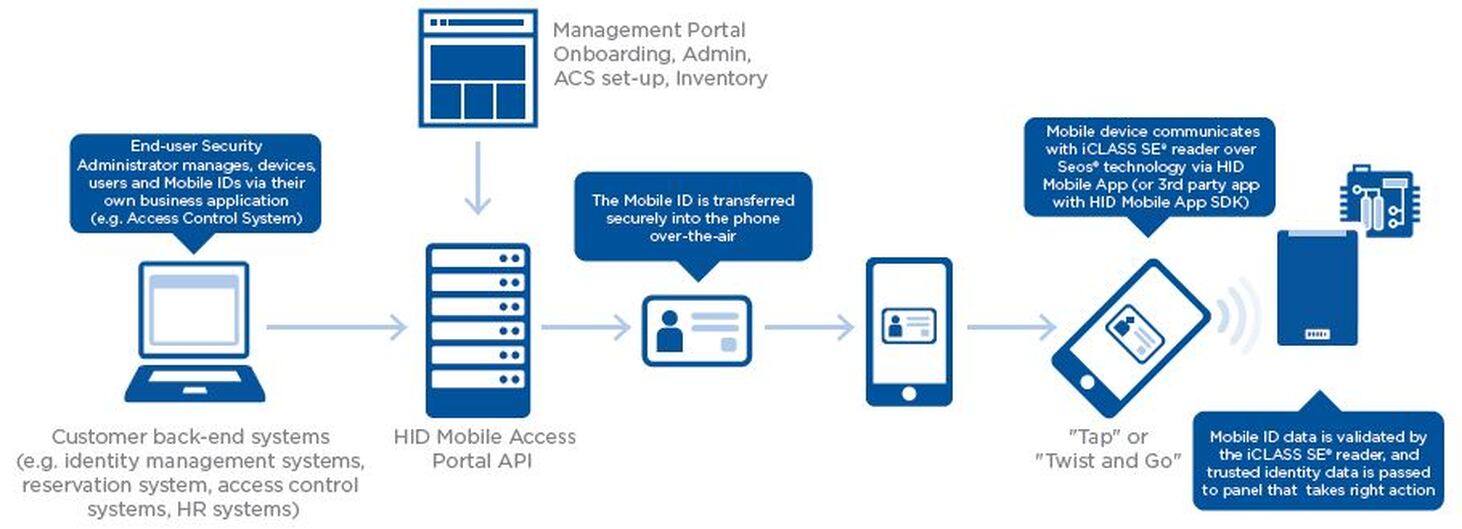
Integrating Multi-Factor Authentication in Complex IT Environments
Integrating Multi-Factor Authentication With the adaptation to remote workforces as a result of the pandemic, internet usage across industries has increased. Cybercriminals capitalized on the trend and aimed their attacks on businesses that rely on cloud-based applications, online data storage, and many other digital assets. According to the U.S FBI, cybercrimes sparked 300% since the… View Article

HID Tech Talk: Product Trends and What’s In Store for 2022
ADVANTIDGE Technology & Security Trends; What’s in Store for 2022 Business Operations Whether you’re an IT or Security leader, part of an enterprise looking to achieve industry compliance, or an innovation enthusiast, many of the tech and security trends below lend us some insight into 2022 business initiatives. 1. Transition from On-Prem to Cloud Based … View Article
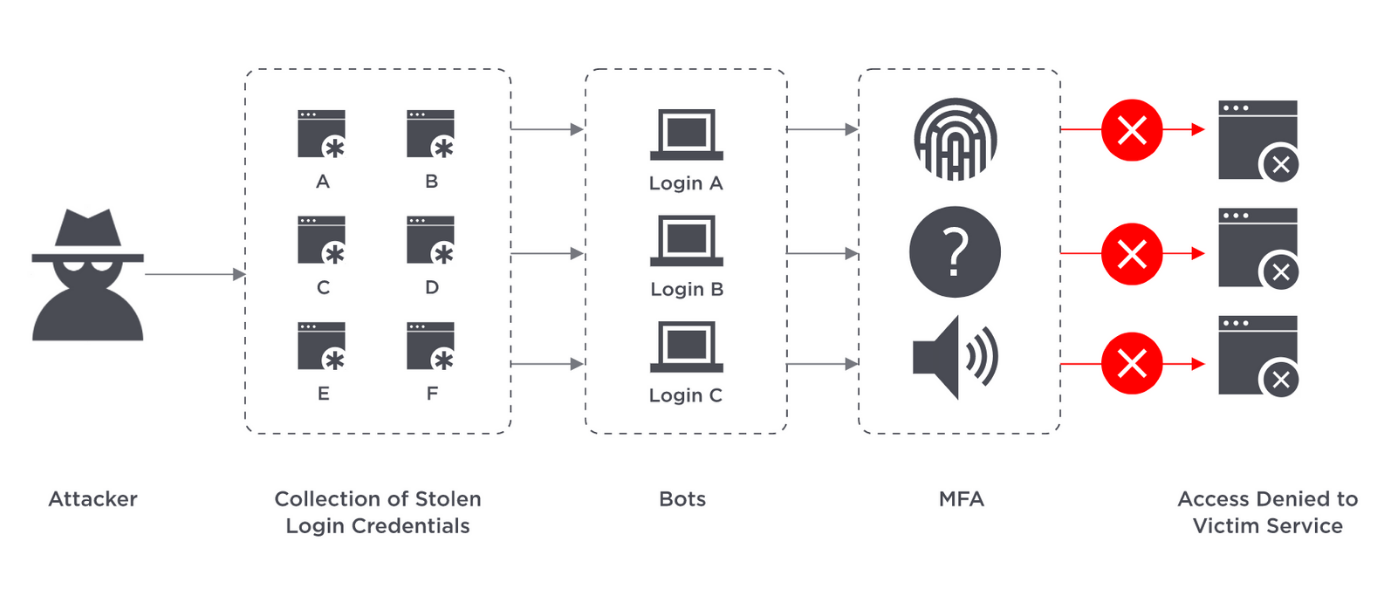
How Does Multi-Factor Authentication Prevent Cybersecurity Breaches?
Cybersecurity breaches are not a matter of if, they’re a matter of when. In Verizon’s 2021 Data Breach Investigation Report, phishing remains one of the top security threats and has increased to 36% of breaches, up from 25% last year. The increase correlates with the massive shift to work-from-home employees following the pandemic. Criminals target… View Article

How Visitor Management Systems Verify Legitimate ID Cards
Visitor Management Software Confirms Legitimate Guests What types of technologies does your organization use to prepare your workforce for incoming customers and visitors? What verification processes does your visitor management system have to detect illegitimate ID’s, if any? Check out the Visitor Management Checklist below to determine if your organization has the technology in place… View Article